With features such as Pass Through Authentication (PTA) available in AD Connect, there are really very few use cases for ADFS federation any more. I encourage anyone still using ADFS for Office 365 / Azure AD to review if they still need to maintain (a minimum) of four ADFS servers and a number of firewall ports inbound (to DMZ). In the past moving from ADFS wasn’t overly difficult but did carry some risk as each domain needed to be converted to manually, not allowing for granular rollout to specific users for testing. This was particularly worrying for very large organizations who need to test changes before potentially impacting thousands of users. One workaround to test moving away from ADFS was to use a lightly used domain to convert first, testing with a smaller user count but not every organization have a domain already federated with a small amount of users assigned.
To make this process easier, last year Microsoft added support for staged rollout of cloud authentication, allowing you to move users from federated authentication to managed without cutting over the entire domain. This also opens up the possibility to test out some of the cool Identity Protection features available through Azure AD on a select group without impacting users. We can use this method for up to 50,000 users so our test cases should be more than achievable.
Configure AD Connect
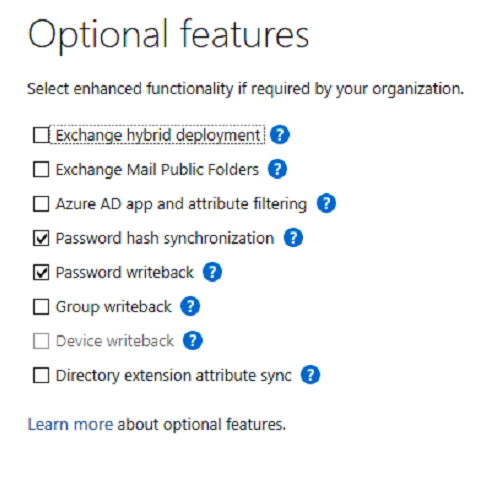
Before getting started, ensure that your chosen target authentication method has been configured on your AD Connect servers. Supported scenarios are Password Hash, Pass-Through Authentication and Seamless Single Sign-on. You can check or configure this in the AD Connect Wizard Optional Features page as shown in Figure 1.
Create a Group to Scope the Change
To scope the change from federated to managed, create a new Azure AD Security Group similar to the one in Figure 2.

Enable Staged Rollout
Next, to enabled staged rollout for the group we created, open Azure AD and navigate to “AD Connect” -> “Enable staged rollout for managed user sign-in”. From here you can enable the features you want and specify the security group that your created previously as shown in Figure 3.

And that’s it, you can rollout to whoever you see fit for testing. Just remember if you are performing a full cutover at the end to convert the domain to managed and remove the pilot group.


Without enabling password hash from on-prem AD connect, will stage rollout will not work?
LikeLike
Yes that should work. I haven’t tested myself but I see no reason it wouldn’t. You would essentially move users to use pure cloud auth?
LikeLike
How long for it to take effect after adding the users to the group?
LikeLike
From my experience no more than an hour and will be triggered the next time the user is challenged.
LikeLike